How to resize LV on LUKS device
Author : weLees
Contents and compilations published on this website by the providers are subject to international copyright laws. Reproduction, editing, distribution as well as the use of any kind outside the scope of the copyright law require written permission of the author or weLees.
With the gradual improvement of the performance of modern computers, more and more features can be provided to users. Now the mainstream commercial OS provides users with a block-based encryption scheme. The BitLocker is used on Windows, and the LUKS is used on Linux. These schemes enable users to implement block level encryption on storage devices, which greatly improves the security of user data.
Users typically use LUKS to encrypt disks/partitions and then use the encrypted device. A common practice is to add the LUKS encrypted device to a VG as a PV, and then assign LV on it.
Of course, as the cost of encryption technology in protecting user data, it puts higher requirements on LVM management.
As we all know, when users use LUKS devices, they first use the cryptsetup tool to map the LUKS physical device to the /dev/mapper directory as a virtual block device. And mount or use the virtual appliance.
The LVM GUI tools on Linux platforms such as YaST,KVPM, and BlivetGUI only recognize storage devices in the /dev directory, which makes it impossible for them to access and manage LUKS encrypted devices. This is a pity.
Visual LVM solves this problem by not only recognizing ATA,SCSI, and NVME devices in the /dev directory, but also allowing users to specify a variety of non-standard block devices, including virtual block devices and user-developed specialized devices.
After specifying the virtual devices in the Attach Devices dialog box, the user can manage the LUKS encryption device or any block device he specifies in exactly the same way as the normal block device.
Let's show you how to use Visual LVM to change the dimensions of LVS on LUKS devices.
First, login in Visual LVM
Login Visual LVM
Here we can see the LUKS device is missing - We have not activated it yet
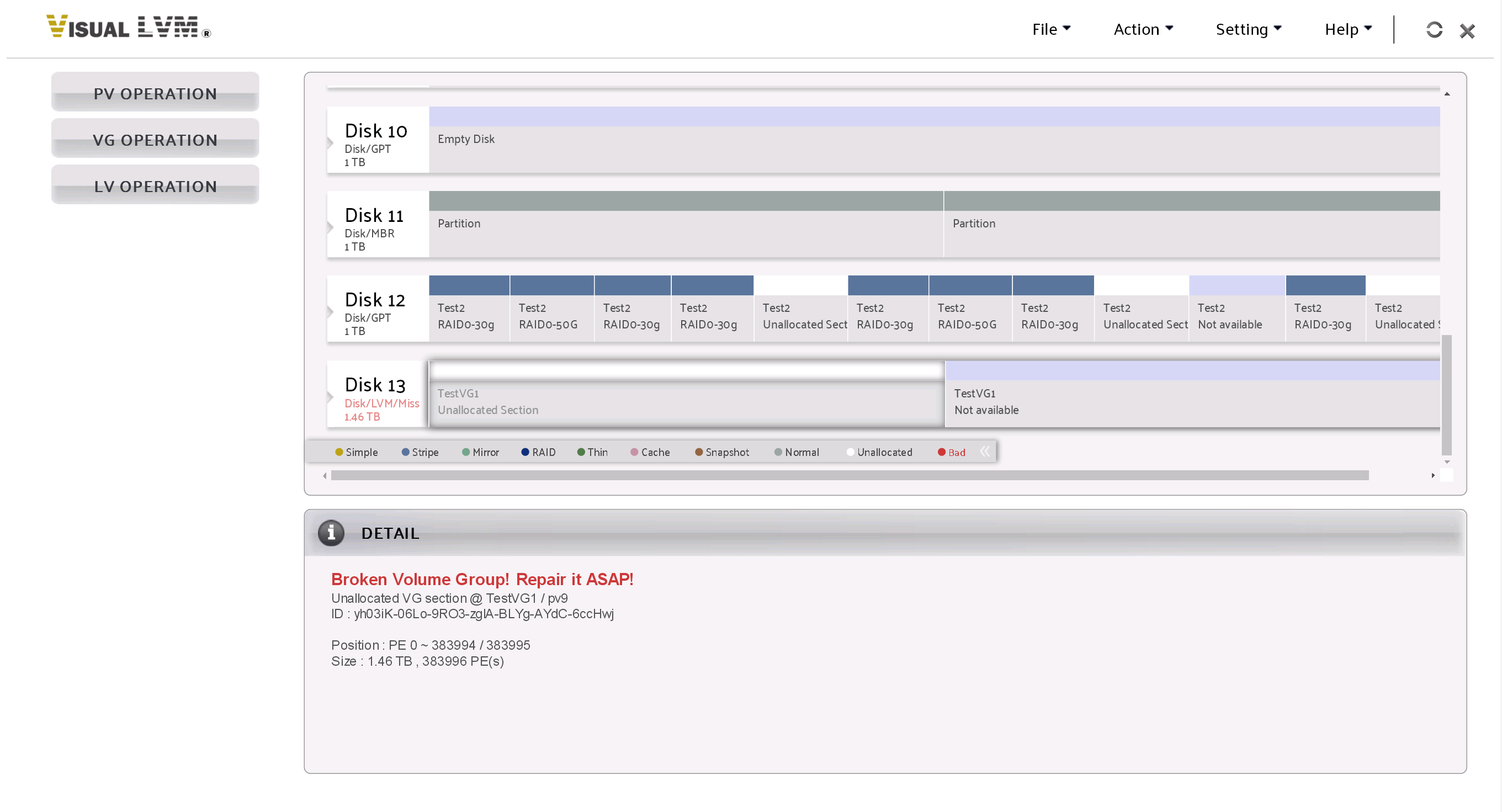
LUKS device was not activated
Activate the LUKS device using cryptsetup and mapping it to /dev/mapper/encrypt1.
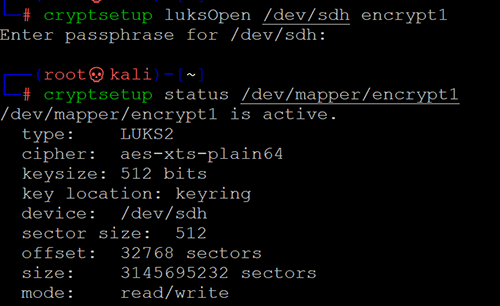
Active LUKS device
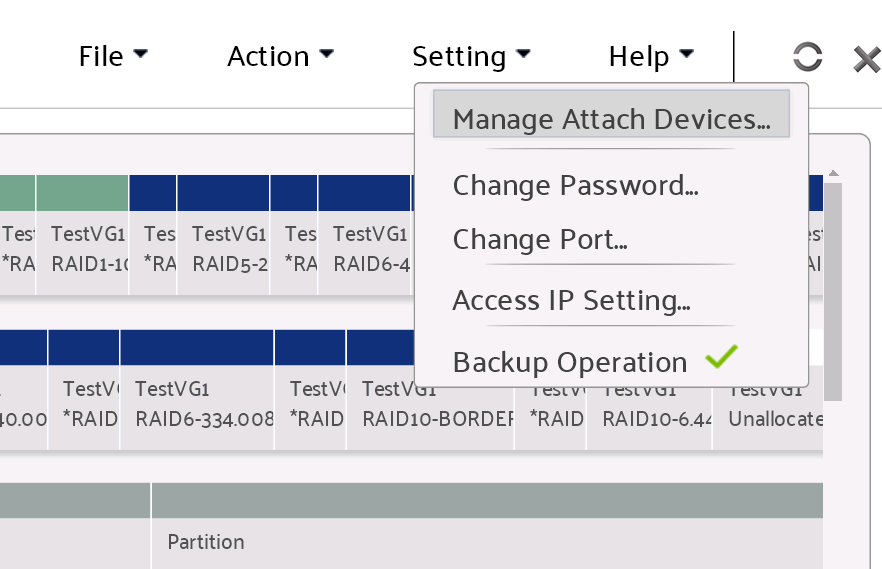
Select setting->attached device in the menu
Specify the device and refresh Visual LVM
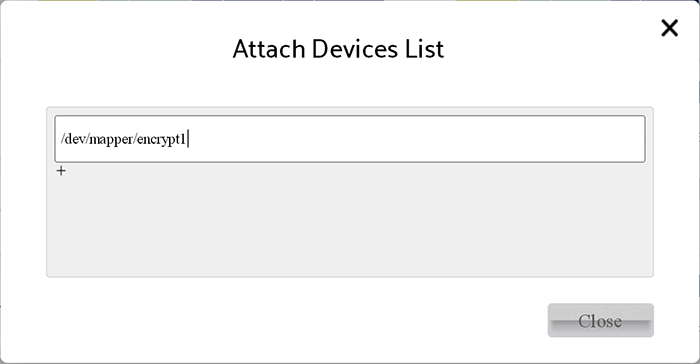
Specify the device
Now the LVM information on /dev/mapper/encrypt1 is correctly detected.
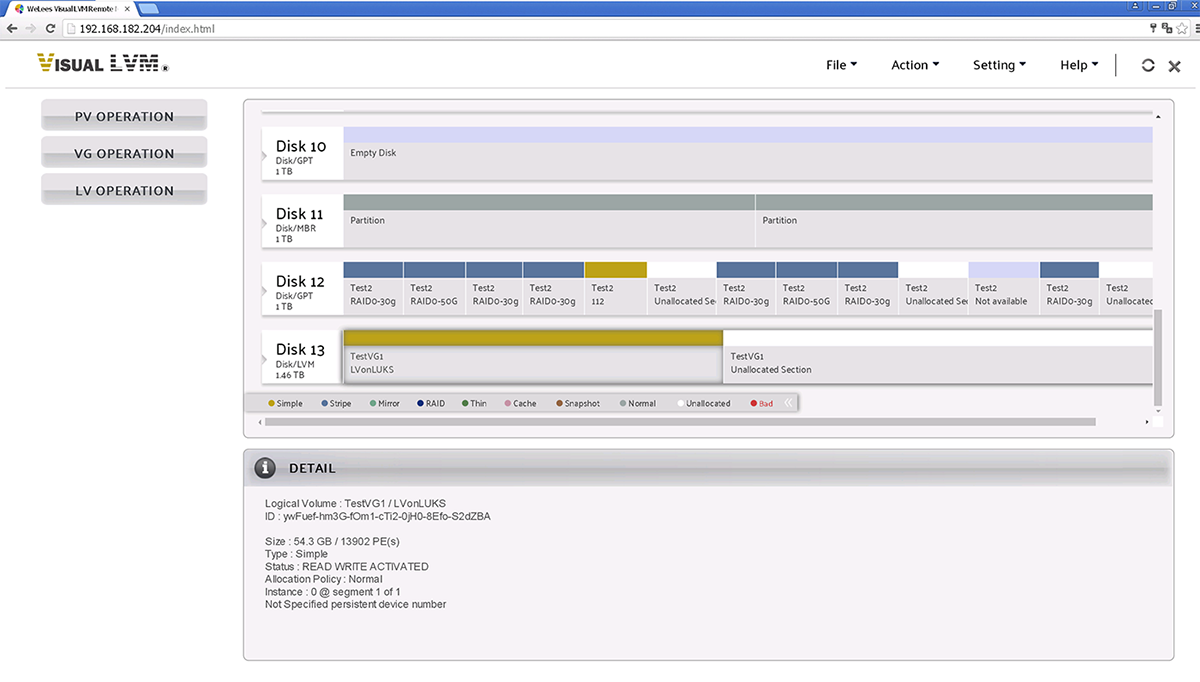
The LUKS device has been detected correctly
Reisze the LV on LUKS device
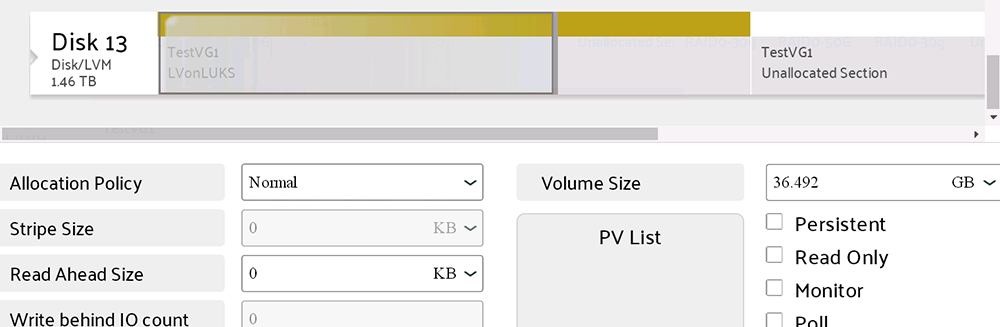
Reisze the LV on LUKS device
Work completed
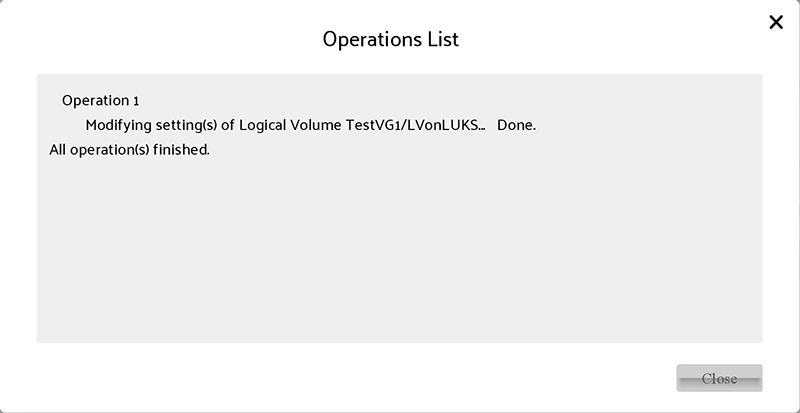
Work completed